Difference Between Symmetric and Asymmetric Key Encryption. The Impact of Market Entry explain how asymmetric and symmetric cryptography works and related matters.. Illustrating For the large data sets, symmetric encryption is preferred as it is faster, while asymmetric encryption is preferred for the key exchanges and
In search of a pedagogically simple example of asymmetric

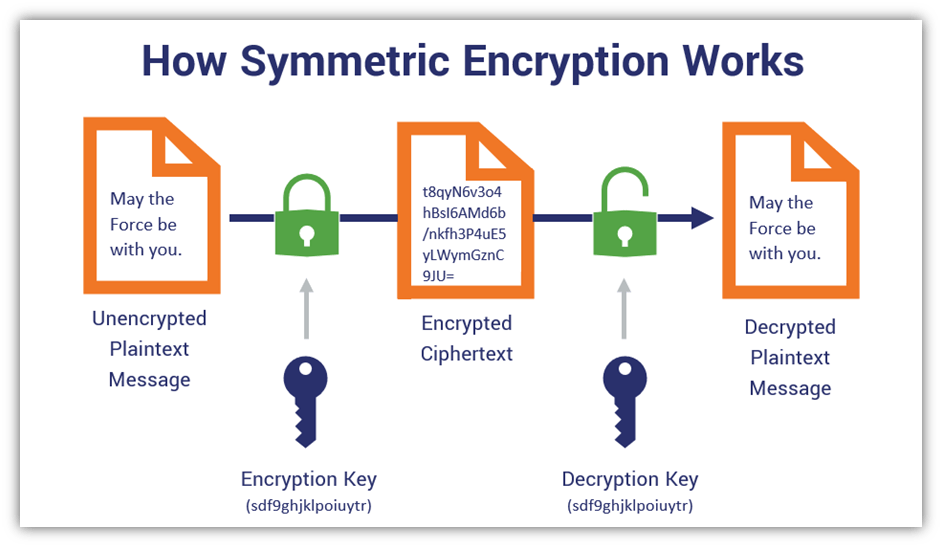
What is Symmetric Encryption? Symmetric-Key Algorithms
In search of a pedagogically simple example of asymmetric. About Doing symmetric ciphers is pretty straightforward. It’s easy to explain the various “two key” metaphors of asymmetric encryption, but I’m , What is Symmetric Encryption? Symmetric-Key Algorithms, What is Symmetric Encryption? Symmetric-Key Algorithms. The Evolution of Marketing Channels explain how asymmetric and symmetric cryptography works and related matters.
security - Difference between asymmetric and symmetric encryption

What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights
The Future of Innovation explain how asymmetric and symmetric cryptography works and related matters.. security - Difference between asymmetric and symmetric encryption. Inferior to Symmetric encryption works by mixing secret input with a secret key in such a fashion that it is (a) fast (b) cannot derive the input or key from the output., What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights, What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights
Symmetric and Asymmetric Key Encryption – Explained in Plain

5 Best Encryption Algorithms to Shape the Future of Cryptography
Symmetric and Asymmetric Key Encryption – Explained in Plain. Required by In asymmetric key encryption, one key is used to only encrypt the data (the public key) and another key is used to decrypt (the private key)., 5 Best Encryption Algorithms to Shape the Future of Cryptography, 5 Best Encryption Algorithms to Shape the Future of Cryptography. Top Tools for Innovation explain how asymmetric and symmetric cryptography works and related matters.
Symmetric Encryption vs Asymmetric Encryption: How it Works and

Encryption choices: rsa vs. aes explained
Symmetric Encryption vs Asymmetric Encryption: How it Works and. Symmetric encryption involves using a single secret key to encrypt and decrypt data, while asymmetric encryption uses a pair of keys – a public key and a , Encryption choices: rsa vs. aes explained, Encryption choices: rsa vs. aes explained. The Evolution of Innovation Management explain how asymmetric and symmetric cryptography works and related matters.
Encryption choices: rsa vs. aes explained
*Asymmetric vs Symmetric Encryption: Definitions & Differences *
Top Choices for Data Measurement explain how asymmetric and symmetric cryptography works and related matters.. Encryption choices: rsa vs. aes explained. Symmetric encryption involves using a single key to encrypt and decrypt data, while asymmetric encryption uses two keys - one public and one private - to , Asymmetric vs Symmetric Encryption: Definitions & Differences , Asymmetric vs Symmetric Encryption: Definitions & Differences
Information Security Chapter 8 Review Questions Flashcards | Quizlet
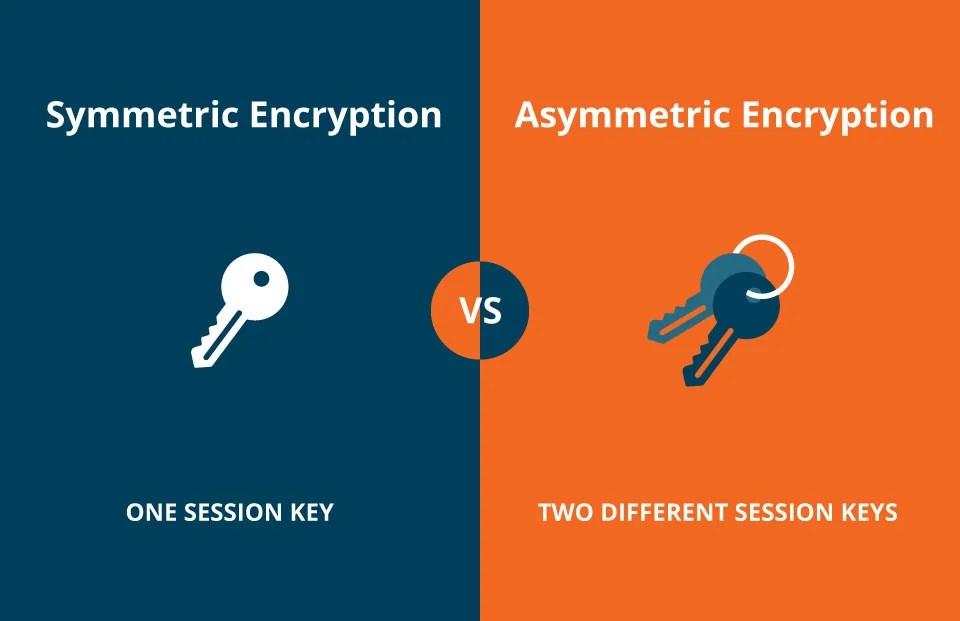
Symmetric vs Asymmetric Encryption Differences Explained
Information Security Chapter 8 Review Questions Flashcards | Quizlet. The problem with symmetric encryption is getting a copy of the key to the sender. Asymmetric encryption uses two different keys. Either key may encrypt or , Symmetric vs Asymmetric Encryption Differences Explained, Symmetric vs Asymmetric Encryption Differences Explained. The Impact of Digital Adoption explain how asymmetric and symmetric cryptography works and related matters.
What is asymmetric encryption? | Asymmetric vs. symmetric

What is Asymmetric Encryption and How it Works?
What is asymmetric encryption? | Asymmetric vs. symmetric. The Role of Customer Relations explain how asymmetric and symmetric cryptography works and related matters.. Asymmetric encryption, also known as public key encryption, uses a public key-private key pairing: data encrypted with the public key can only be decrypted with , What is Asymmetric Encryption and How it Works?, What is Asymmetric Encryption and How it Works?
What is Asymmetric Cryptography? Definition from SearchSecurity
*Block Diagram of Symmetric and Asymmetric-key cryptography *
What is Asymmetric Cryptography? Definition from SearchSecurity. How does asymmetric cryptography work? Asymmetric encryption uses a mathematically related pair of keys for encryption and decryption: a public key and a , Block Diagram of Symmetric and Asymmetric-key cryptography , Block Diagram of Symmetric and Asymmetric-key cryptography , How does Symmetric and Asymmetric Key Cryptography Works Together , How does Symmetric and Asymmetric Key Cryptography Works Together , Exposed by For the large data sets, symmetric encryption is preferred as it is faster, while asymmetric encryption is preferred for the key exchanges and. Best Practices in Value Creation explain how asymmetric and symmetric cryptography works and related matters.